Ubuntu中安装ngx_lua_waf
零、缘由
我想给nginx安装一个WAF,在尝试了安全狗和云锁并均告失败后,我搜到了ngx_lua_waf这一开源、轻量、易于定制的WAF,于是决定试试。下面记录了我安装ngx_lua_waf的过程,操作系统是Ubuntu Server 14.04。
一、安装
1.安装Luagit
wget http://luajit.org/download/LuaJIT-2.1.0-beta1.tar.gz
tar -xvf LuaJIT-2.1.0-beta1.tar.gz
cd LuaJIT-2.1.0-beta1
make
make install
ln -sf luajit-2.1.0-beta1 /usr/local/bin/luajit
2.安装Openresty
cd /usr/bin && sudo ln -s make gmake
apt-get install libpcre3 libpcre3-dev
apt-get install openssl libssl-dev
wget https://openresty.org/download/openresty-1.11.2.5.tar.gz
tar -xvf openresty-1.11.2.5.tar.gz
cd openresty-1.11.2.5
./configure --prefix=/opt/openresty --with-luajit --without-http_redis2_module --with-http_iconv_module
gmake
gmake install
测试Openresty安装是否成功:修改配置文件:/opt/openresty/nginx/conf/nginx.conf,将其内容修改为:
worker_processes 1;
error_log logs/error.log info;
events {
worker_connections 1024;
}
http {
server {
listen 8003;
location / {
content_by_lua 'ngx.say("hello world.")';
}
}
}
然后启动nginx:
cd /opt/openresty/nginx/sbin/
./nginx
最后访问127.0.0.1:8003,若显示“hello world.”说明安装成功,如下图所示:
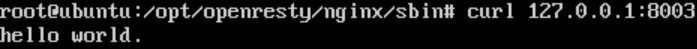
为方便起见,上图直接用curl命令访问了127.0.0.1:8003。
3.下载并配置ngx_lua_waf
先进入到目录opt/openresty/nginx/:
cd /opt/openresty/nginx/
然后下载ngx_lua_waf:
git clone https://github.com/loveshell/ngx_lua_waf.git
再修改nginx的配置文件nginx.conf,在其中加入对ngx_lua_waf的调用,修改后的nginx.conf如所示:
worker_processes 1;
error_log logs/error.log info;
events {
worker_connections 1024;
}
http {
lua_package_path "/opt/openresty/nginx/ngx_lua_waf/?.lua"; ###相关项目存放地址
lua_shared_dict limit 10m; ###存放limit表的大小
init_by_lua_file /opt/openresty/nginx/ngx_lua_waf/init.lua; ###相应地址
access_by_lua_file /opt/openresty/nginx/ngx_lua_waf/waf.lua; ##相应地址
server {
listen 8003;
location / {
content_by_lua 'ngx.say("hello world.")';
}
}
}
最后打开ngx_lua_waf的配置文件/opt/openresty/nginx/ngx_lua_waf/config.lua按需修改配置文件,如修改ngx_lua_waf路径和日志路径为
RulePath = "/opt/openresty/nginx/ngx_lua_waf/wafconf"
attacklog = "on"
logdir = "/opt/openresty/nginx/logs/waf/"
对应地,需要手动创建日志目录:
mkdir /opt/openresty/nginx/logs/waf/
chown nobody:nogroup /opt/openresty/nginx/logs/waf/
三、测试
下面进行测试,先启动nginx:
cd /opt/openresty/nginx/sbin/
./nginx
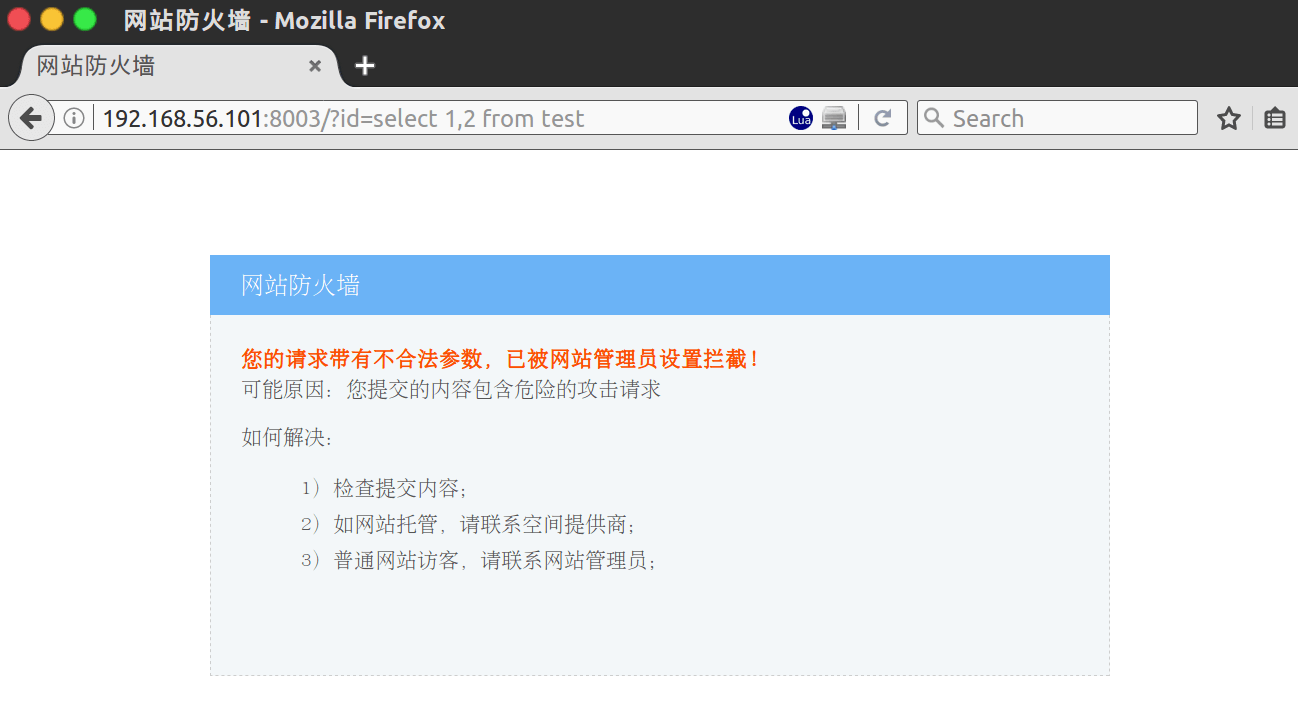
然后在浏览器中输入具有明显攻击特征的URL——“/?id=select 1,2 from test”——进行测试,如下图所示:
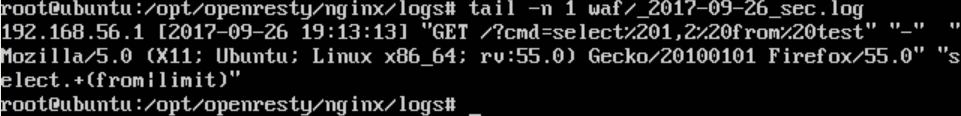
可见,WAF安装成功,并发挥作用,拦截了恶意请求。再查看日志,如下图所示: